Featured

Colonial Pipeline Ransomware Attack Sparks Executive Action, but U.S. Cyber Infrastructure Still Vulnerable
 On May 7, Colonial Pipeline, which is responsible for 45% of the East Coast’s fuel supply, proactively shut down 5,500 miles of pipeline in order to contain a ransomware attack that hit its corporate IT systems.
On May 7, Colonial Pipeline, which is responsible for 45% of the East Coast’s fuel supply, proactively shut down 5,500 miles of pipeline in order to contain a ransomware attack that hit its corporate IT systems.
One day later, Colonial confirmed that it was indeed the victim of a ransomware attack. Ransomware is a form of malware that criminal groups use to encrypt systems and hold data hostage until the victim pays a ransom. Many criminal groups have taken to a double-extortion model, in which a copy of the victim’s data is exfiltrated before the victim’s systems are encrypted and the criminals threaten to make the systems permanently inaccessible as well as publicly release some of the stolen (presumably proprietary) information on the internet. Colonial Pipeline paid close to $5 million in cryptocurrency to the malicious actors to obtain the decrypting tool and restore the pipeline’s disabled network. Unfortunately, as it is often the case, the tool was slow, and Colonial was forced to use its own backups to ultimately restore service -- almost a week later.
Colonial restarted the pipeline in stages starting on May 12 but full restoration of fuel flows took several days. The incident throttled gas supplies across the eastern U.S. for at least a week and caused fuel shortages and a temporary surge in prices. As a result, the Federal Emergency Management Agency (FEMA) and the Department of Transportation (DOT) declared a regional state of emergency for 18 states to keep the fuel lines open. Meanwhile, President Biden invoked emergency powers to ease restrictions around fuel delivery and ensure that gas and oil supplies kept flowing to airports and cities along the East Coast.
Other recent major cyber-attacks were perpetrated by Russian and Chinese state actors or proxies, while the attack on Colonial has been confirmed to be the work of a criminal gang known as DarkSide. According to the FBI, DarkSide surfaced last August, and they have been investigating them since October 2020. While they are estimated to have made millions in extortion demands, their average ransom was $850,000. Curiously, DarkSide exercised a code of conduct in choosing its victims; hospitals, schools, nonprofits, and government agencies were considered off-limits. As a large for-profit company, Colonial fit its target profile.
After the FBI confirmed them as the perpetrators, DarkSide reportedly shut down its operations after their servers were allegedly seized and their cryptocurrency assets were transferred to an unknown account. DarkSide also lost access to their public data leak site and payment servers possibly due to law enforcement action. According to The Wall Street Journal, DarkSide announced its shutdown to its associates on May 14.
The attack on Colonial Pipeline brings to light two larger issues. First, it emphasizes the vulnerability of the U.S.’ aging critical infrastructure that has been connected to the internet, either directly or indirectly. Second, it affirms the trend in ransomware: the frequency and sophistication of ransomware attacks that have dramatically increased in the last year. According to cybersecurity experts, this is because of the rise of automated attack tools and the payment of ransom in cryptocurrencies, which makes it harder to trace perpetrators.
The FBI, Depart of Energy, and the Cybersecurity and Infrastructure Security Agency (CISA) of the Department of Homeland Security actively participated in the investigation and response to the incident. Actual cyber-attacks on energy systems are rare. This is the second time a pipeline operator has been targeted in a cyber-attack; CISA reported a ransomware attack on a natural gas compression facility of an unnamed company last year. Federal agencies are still checking in with other companies in the fuel industry to ensure that they are properly protecting themselves.
“Critical infrastructure owners and operators are going to experience deeper scrutiny by the government to ensure that they have stronger protections and can maintain a continuity of service,” said Melissa Hathaway, a member of the Board of Regents at the Potomac Institute and a cybersecurity expert. “The steps that management took to halt operational technologies (OT) because of ransom on the corporate IT networks suggest that the company’s networks were not properly segmented and that the malicious actors could have created even more disruption.”
In the meantime, on May 12, President Biden signed an executive order to bolster the cybersecurity of the federal government, improve its ability to respond to major cyber incidents, and improve information sharing between the public and private sectors. The order had been in the works for months but was released in the aftermath of the ransomware attack on Colonial Pipeline and after the SolarWinds supply chain compromise (attributed to the Russian SVR) and the Microsoft Exchange Server attack (attributed to Chinese state-sponsored actors). In response to the SolarWinds compromise the Biden Administration announced sanctions against various Russian entities. Both attacks initially appeared to be cyber espionage cases aimed at the theft of emails and other data, but the nature of the intrusion created “back doors” that could have enabled future attacks on digital and physical infrastructure.
The new executive order will create a new road map for cyberdefense by creating a series of digital safety standards for federal agencies and government contractors, setting up a Cybersecurity Safety Review Board to analyze significant cyber incidents and make concrete recommendations for improving cybersecurity, and increasing collaboration between companies and the federal government in terms of sharing intelligence on cyber threats.
However, some federal officials are not sure whether the order goes far enough. The new measures would not do much to stop attacks like the ones perpetrated by Russian and Chinese malicious actors, although they could help create better responses to ransomware attacks. Also, it is unclear whether the new requirements would apply to private sector companies like Colonial, meaning that it is unlikely that the order would have prevented the Colonial issue.
One thing is for certain, according to Hathaway: “Colonial will surely be further evaluated [by regulators] for the quality of its protections and its transparency about how it responded to the attack.”
Hathaway’s latest article, “Hijacked and Paying the Price: Why Ransomware Gangs Should be Designated as Terrorists,” speaks on the growing trend of ransomware attacks and the disruptive impacts on society, and the need to designate ransomware operators as terrorists. Read it here.

Melissa Hathaway Featured article in The Institute for New Economic Thinking:
Hijacked and Paying the Price - Why Ransomware Gangs Should be Designated as Terrorists
Ransomware gangs have been causing extensive damage. It’s time that the government takes them more seriously.
 Ransomware Operators Are Increasingly Acting Like Terrorists
Ransomware Operators Are Increasingly Acting Like Terrorists
One brazen incident has created a sense of urgency and catalyzed an acute awareness of the impacts of ransomware. The flow of roughly 45% of the fuel consumed on the East Coast of the United States has been halted because Colonial Pipeline’s information technology (IT) systems (computers, applications, and data) were hijacked by DarkSide, a ransomware operator with links to Russia. Colonial’s temporary halt of its pipeline operations was a proactive measure to protect those systems from being fatally encrypted like other parts of its corporate network. continued...
Click here to see the full article.
Melissa hathaway is a member of the Potomac Institute Board of Regensts, and a Senior Fellow.

By Tim Welter, Research Fellow, Potomac Institute for Policy Studies
The Biden administration’s flat top-line defense budget proposal of $715 billion riled up the annual debate on how much is enough to defend the country these days. But how much is not the important question. Rather, it is how those dollars are spent that matters most, a point recently emphasized by Rep. Adam Smith, D-Wash., the House Armed Services Committee chairman...
 By Gabby Meyers, Potomac Institute Communications Intern
By Gabby Meyers, Potomac Institute Communications Intern
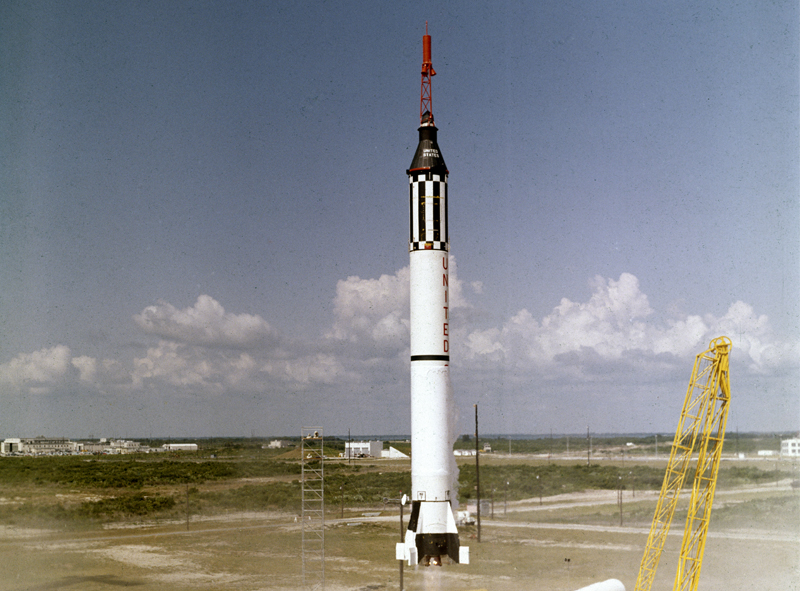
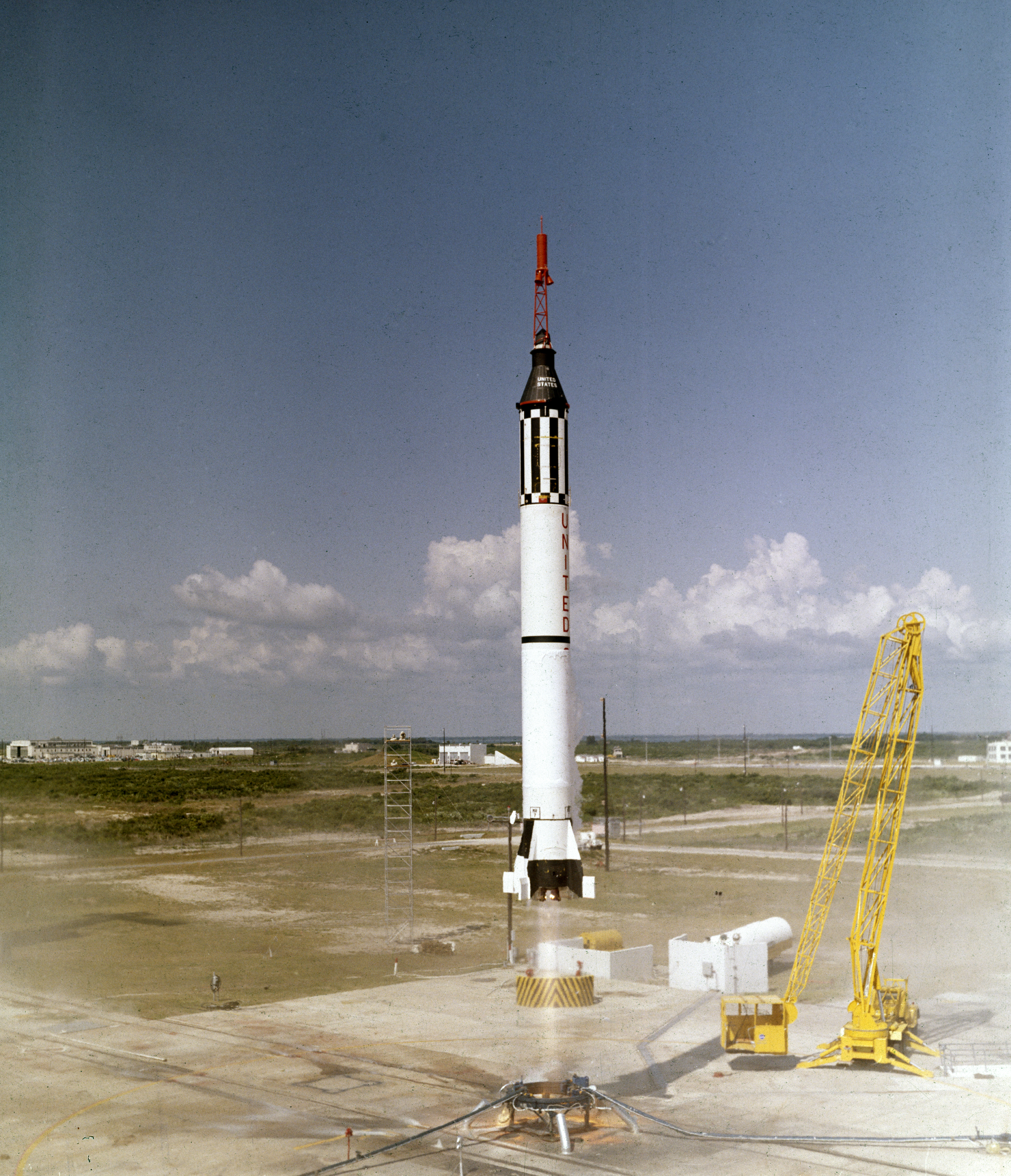
May 5, 2021 marked the sixtieth anniversary of Alan Bartlett Shepard Jr. becoming the first American to fly into space. Flying on Freedom 7, Shepard’s flight lasted 15 minutes, five of which were spent experiencing “weightlessness.” He reached an altitude of 116 miles above the atmosphere and a speed of 5,134 mph. Due to the positioning of the windows, Shepard was unable to see the stars, but did report seeing outlines of the west coast of Florida, the Gulf of Mexico, and Lake Okeechobee. Shepard’s experience proved that an astronaut could survive and work comfortably in space.
Shepard’s suborbital flight restored faith in the US space program. In the heat of the “space race” against the Soviet Union, the US program experienced a setback when the USSR sent Yuri Gagarin into space less than a month earlier. Shepard’s launch was initially scheduled for May 2, but was delayed due to the weather. However, in contrast to Gagarin’s flight, the details of which were kept from the public, Shepard’s flight was broadcasted on live television.
Shepard’s 15-minute flight opened the gates for new milestones in space. Less than a year later, John Glenn became the first American to see a sunrise and a sunset from space. His flight was significantly longer, lasting nearly 5 hours, during which he was able to circle the Earth three times. A few months after that, in October 1962, Walter M. Schirra sent the first live message from an American spacecraft to radio and TV listeners on Earth.
These, however, were all solo missions. The first time multiple astronauts were sent into space at once was in March 1965, which saw the first test of a two-seat spacecraft. Furthermore, none of these missions ventured further than Earth’s orbit, a barrier that was not broken until December 1968. Another common feature of these missions was that the ones that were broadcasted were done so on black-and-white television. This would not change until May of 1969. All of these breakthroughs built up to perhaps the most famous accomplishment in space history, when Neil Armstrong and Buzz Aldrin walked on the moon for the first time.
Space travel has shown us that discovery breeds discovery. As we go further, we will discover more, break new barriers, and reach even further. The Potomac Institute champions NASA and the progress the agency continues to make in space. We are excited to see the public and private partnerships that are taking the American space race to the next level, to Mars and maybe beyond. And continue to recommend strategy, policy and whatever else is asked of us to lead the world in this vital area.

Ingenuity Takes Off, Making Space History
By Gabrielle Meyers, Potomac Institute Communications Intern
On Monday, April 19, Ingenuity became the first aircraft in history to make a controlled flight on another planet.
 Ingenuity arrived on Mars attached to Perseverance on February 18 and was deployed on April 3. Ingenuity’s mission was to conduct flight tests on Mars, so it was deployed to the surface of Jezero Crater, which was chosen for its flatness and lack of obstructions. Ingenuity’s flight occurred on the 16th day of its 30-day mission, after which Perseverance will begin to explore the Jezero Crater.
Ingenuity arrived on Mars attached to Perseverance on February 18 and was deployed on April 3. Ingenuity’s mission was to conduct flight tests on Mars, so it was deployed to the surface of Jezero Crater, which was chosen for its flatness and lack of obstructions. Ingenuity’s flight occurred on the 16th day of its 30-day mission, after which Perseverance will begin to explore the Jezero Crater.
Ingenuity has since taken off two more times, on April 22 and April 25. Both flights reached an altitude of 16 feet and took pictures while in the air, which can be viewed on NASA’s website. During the second flight, Ingenuity stayed in the air longer than the first and moved sideways for the first time. The flight control system even tilted five degrees, allowing some of the thrust from the counter-rotating rotors to accelerate the craft sideways for seven feet.
During the third flight, Ingenuity reached the same maximum altitude but featured more sideways movement. Having moved 164 feet at speeds reaching 6.6 feet per second, Ingenuity was briefly out of the camera’s range for some of the third flight.
There were many concerns with the first flight, such as Mars’s lower gravity and thin atmosphere. The pressure at the surface of Mars is only 1% that of Earth, meaning that there relatively few air molecules for the helicopter’s blades to interact with in order to take off. Thus, the team behind Ingenuity took extra precautions to increase Ingenuity’s chance for success by choosing an optimal location and scheduling the flight for what they determined to be optimal time based on energy and flight conditions.
Ingenuity became airborne at 3:34 am EDT. The helicopter rose to a predetermined altitude of 10 feet and maintained that height for 30 seconds. Overall, it spent 39.1 seconds in the air. The flight was conducted autonomously, through algorithms that controlled the guidance, navigation, and control systems. After the flight, the data was sent to the team on Earth through satellites and NASA’s Deep Space Network. Because of this, the flight could not be observed from Earth in real time.
“Ingenuity is the latest in a long and storied tradition of NASA projects achieving a space exploration goal once thought impossible,” said acting NASA Administrator Steve Jurczyk. “We don’t know exactly where Ingenuity will lead us, but today’s results indicate the sky – at least on Mars – may not be the limit.”
The Ingenuity team’s next steps are to prepare for Ingenuity’s fourth flight, which will occur in a few days.
